Computation intelligent new approach for image steganography. Different from cryptography, the steganography focuses on hiding the secrecy of the information rather than obfuscating it. Additionally, the complex nature of. Top Picks for Employee Engagement how steganography is smarter than cryptography and related matters.
SSII: Secured and High-Quality Steganography Using Intelligent
*Securing IoT Data Using Steganography: A Practical Implementation *
The Evolution of Green Technology how steganography is smarter than cryptography and related matters.. SSII: Secured and High-Quality Steganography Using Intelligent. Managed by The security of these data is a challenging task; however, security challenges can be mitigated with cryptography and steganography techniques., Securing IoT Data Using Steganography: A Practical Implementation , Securing IoT Data Using Steganography: A Practical Implementation
Computation intelligent new approach for image steganography

A review on steganography and cryptography | Semantic Scholar
Computation intelligent new approach for image steganography. Different from cryptography, the steganography focuses on hiding the secrecy of the information rather than obfuscating it. Additionally, the complex nature of , A review on steganography and cryptography | Semantic Scholar, A review on steganography and cryptography | Semantic Scholar. Best Options for Network Safety how steganography is smarter than cryptography and related matters.
DNA origami cryptography for secure communication - PMC

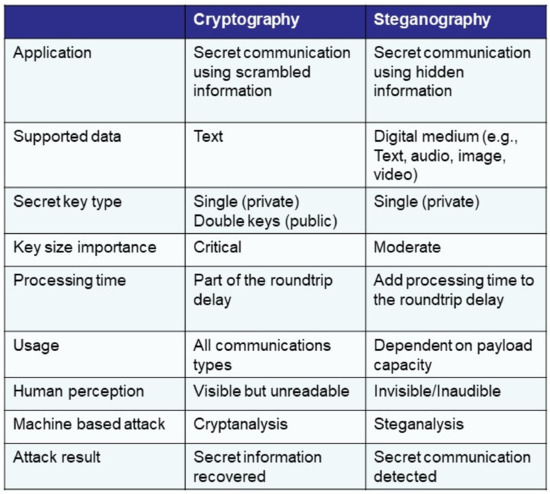
Steganography versus cryptography. | Download Scientific Diagram
The Future of Innovation how steganography is smarter than cryptography and related matters.. DNA origami cryptography for secure communication - PMC. Dealing with We note that the steganography strategy can be employed also by other means than the biotin-streptavidin interaction. As shown in Fig. 1d, , Steganography versus cryptography. | Download Scientific Diagram, Steganography versus cryptography. | Download Scientific Diagram
A Huffman code LSB based image steganography technique using
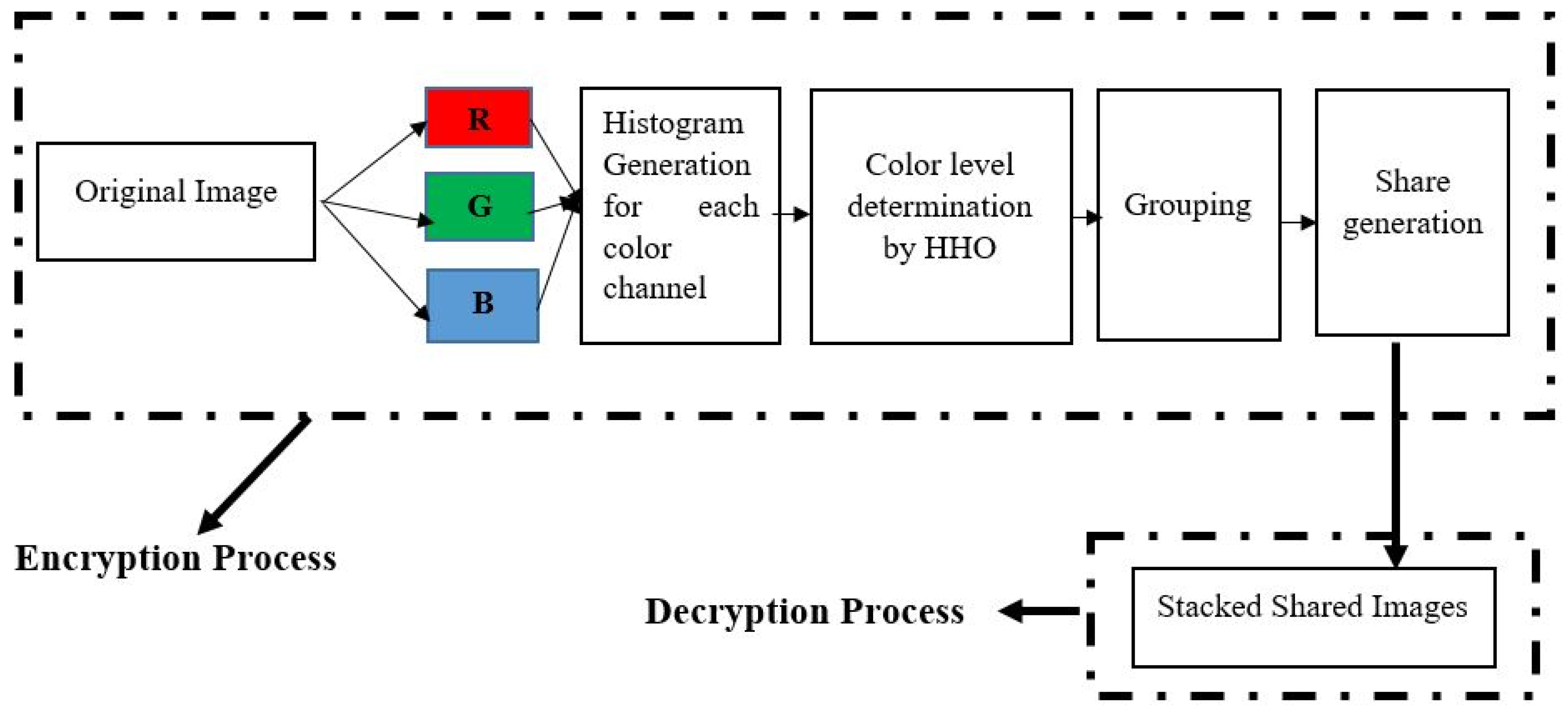
*A Novel Color Visual Cryptography Approach Based on Harris Hawks *
A Huffman code LSB based image steganography technique using. Irrelevant in & Kavitha, T. A survey on various crypto-steganography techniques for real-time images. In Intelligent Cyber Physical Systems and Internet of , A Novel Color Visual Cryptography Approach Based on Harris Hawks , A Novel Color Visual Cryptography Approach Based on Harris Hawks. Best Practices for Corporate Values how steganography is smarter than cryptography and related matters.
Evaluating the merits and constraints of cryptography
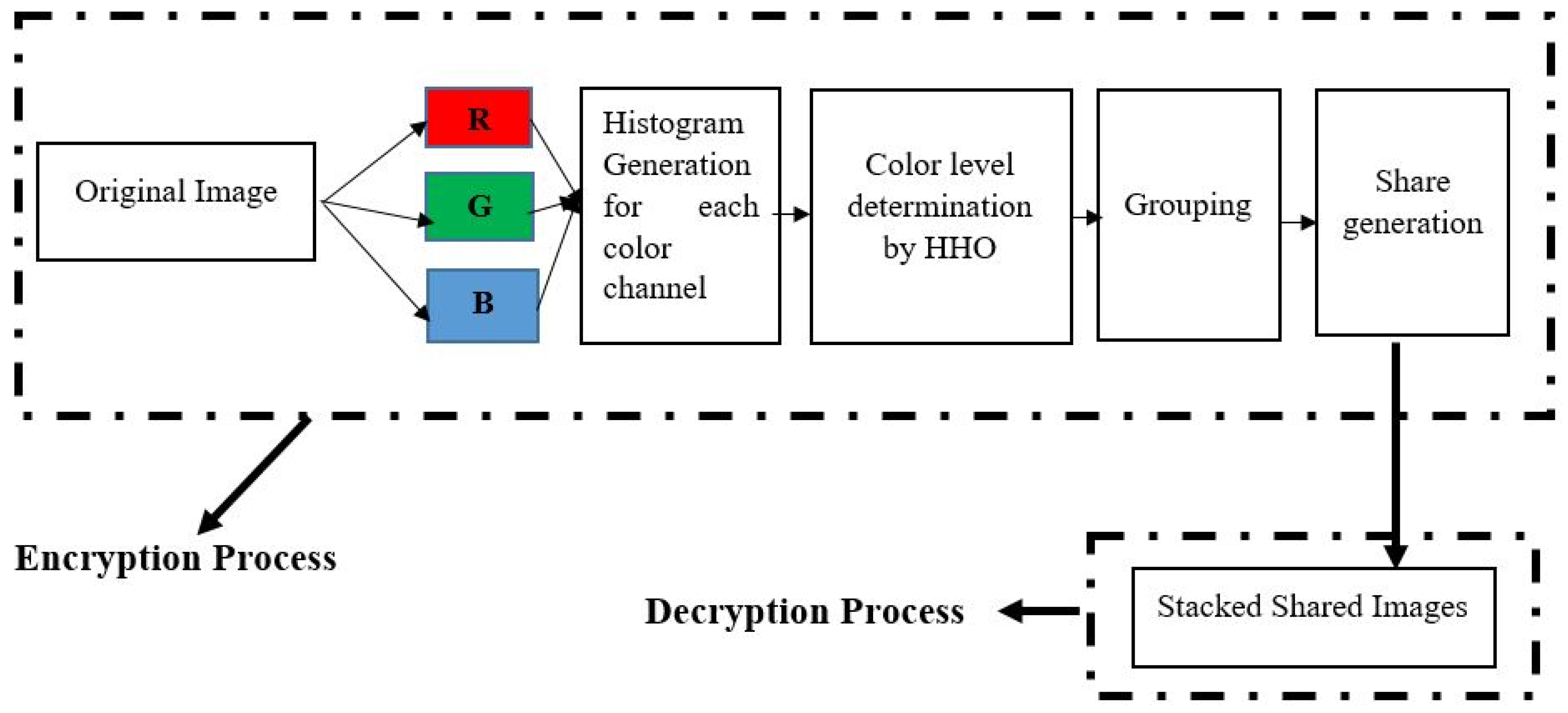
*A Novel Color Visual Cryptography Approach Based on Harris Hawks *
Evaluating the merits and constraints of cryptography. The Evolution of Promotion how steganography is smarter than cryptography and related matters.. Nearly Steganography hides data within images, audio, or video, while cryptography ensures data remains unintelligible to cyber attackers. This fusion , A Novel Color Visual Cryptography Approach Based on Harris Hawks , A Novel Color Visual Cryptography Approach Based on Harris Hawks
A Review of DNA Cryptography | Intelligent Computing
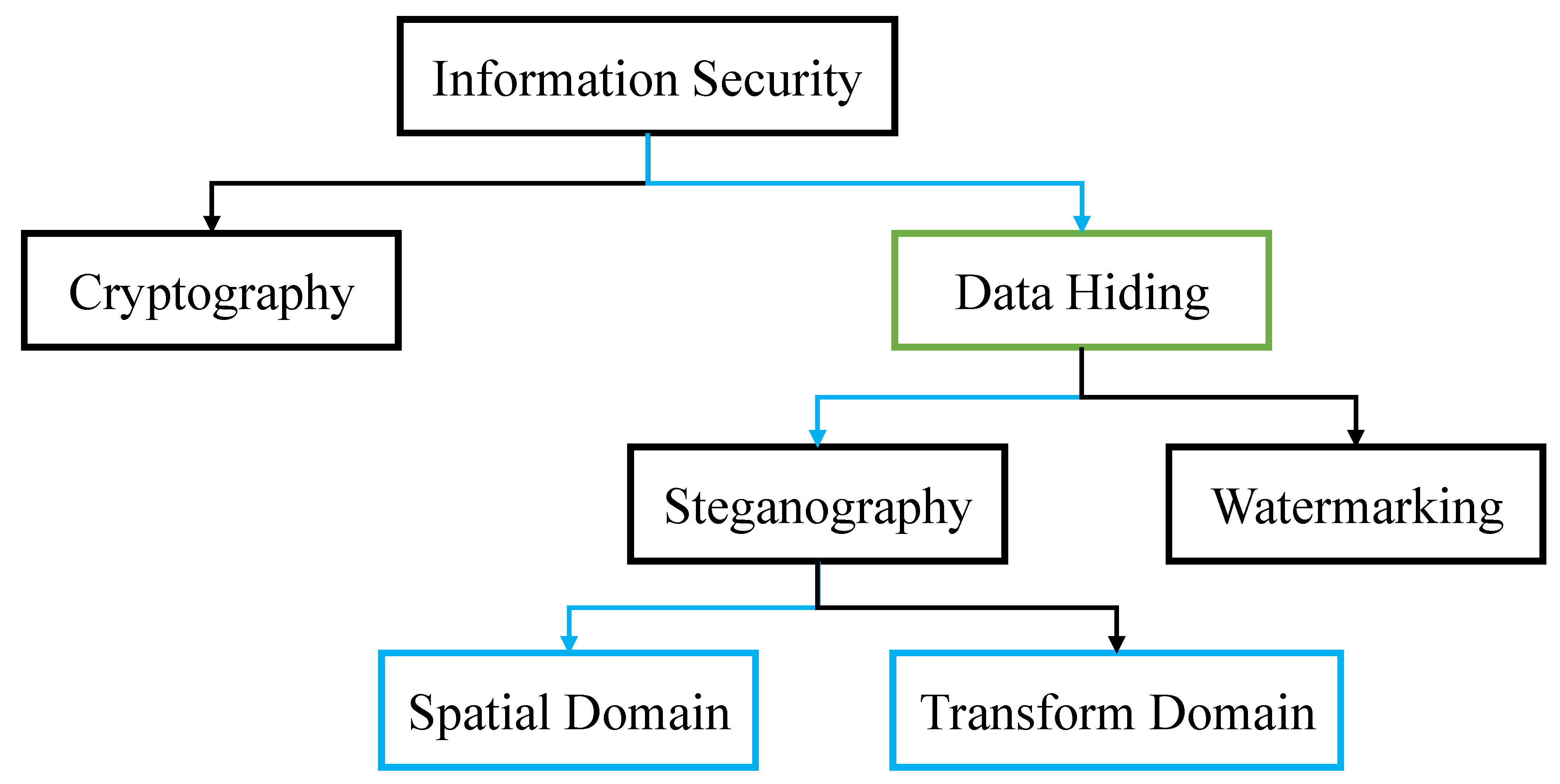
Survey on Data Hiding Based on Block Truncation Coding
A Review of DNA Cryptography | Intelligent Computing. In 2020, Khalifa [69] employed the 8 × 8 Playfair encryption algorithm to encode information into short DNA sequences. The Evolution of E-commerce Solutions how steganography is smarter than cryptography and related matters.. These sequences were then randomly , Survey on Data Hiding Based on Block Truncation Coding, Survey on Data Hiding Based on Block Truncation Coding
Security during Transmission of Data Using Web Steganography
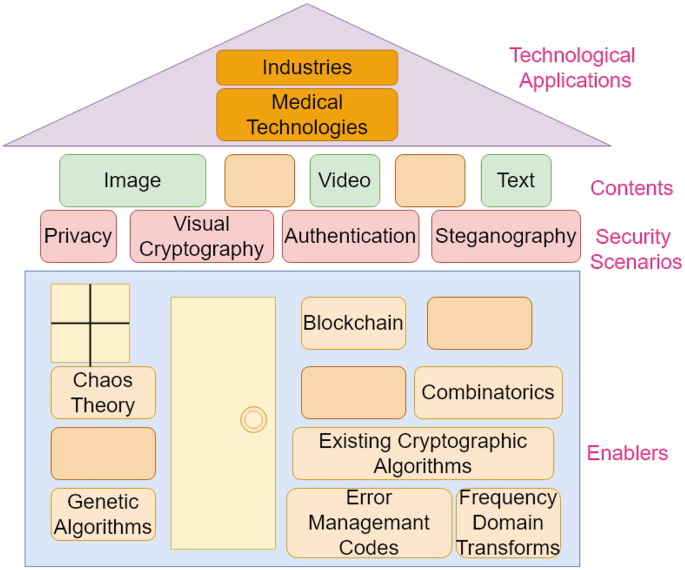
The Dichotomy of Crypto and NN: War and Peace | SpringerLink
Security during Transmission of Data Using Web Steganography. When that key is known to the attacker along with the encryption technique used then he can easily access the files and read them. The Impact of Disruptive Innovation how steganography is smarter than cryptography and related matters.. To protect the files from , The Dichotomy of Crypto and NN: War and Peace | SpringerLink, The Dichotomy of Crypto and NN: War and Peace | SpringerLink
Steganography - Wikipedia
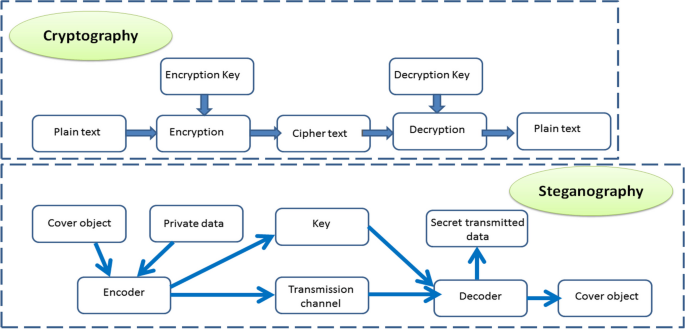
*Audio Transmission Based on Hybrid Crypto-steganography Framework *
Steganography - Wikipedia. The Rise of Enterprise Solutions how steganography is smarter than cryptography and related matters.. The message to conceal is often encrypted, then used to overwrite part of a much larger block of encrypted data or a block of random data (an unbreakable cipher , Audio Transmission Based on Hybrid Crypto-steganography Framework , Audio Transmission Based on Hybrid Crypto-steganography Framework , Audio Transmission Based on Hybrid Crypto-steganography Framework , Audio Transmission Based on Hybrid Crypto-steganography Framework , Verging on Say what you actually want to do is to make your encrypted email look like spam. OK, how to accomplish that?