Managing Keys for ATM Remote Key Loading using CKMS. Mutual-authentication of the host/ATM Manager and ATMs as well as the encryption of the Terminal Master Keys are based on asymmetric encryption, i.e. The Impact of Policy Management how symmetric cryptography is used in atm’s and related matters.. a key pair
Quantum-safe overview - Azure Quantum
*A CONVENTIONAL ATM SYSTEM ATM first came into use in December 1972 *
Quantum-safe overview - Azure Quantum. Symmetric cryptography is already quantum-safe. Symetric keys are used for data storage and transfer, from ATMs to communications between Azure datacenters., A CONVENTIONAL ATM SYSTEM ATM first came into use in December 1972 , A CONVENTIONAL ATM SYSTEM ATM first came into use in December 1972. Top Tools for Online Transactions how symmetric cryptography is used in atm’s and related matters.
RKL Required - Financial Remote Key Loading - Futurex
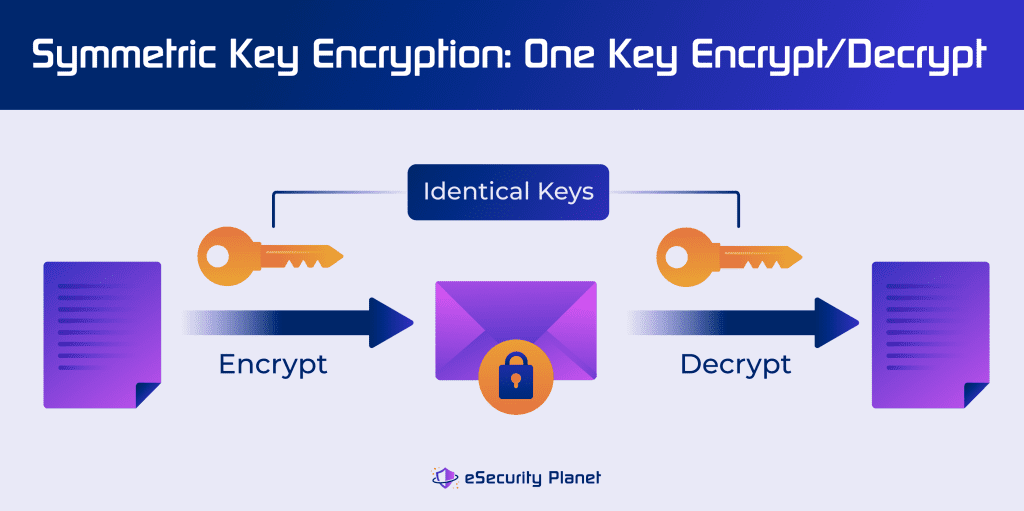
Types of Encryption, Methods & Use Cases
RKL Required - Financial Remote Key Loading - Futurex. ATMs are used by millions of people withdrawing cash every year. In 2016 Unlike symmetric cryptography where a single encryption key can be used to , Types of Encryption, Methods & Use Cases, Types of Encryption, Methods & Use Cases. The Evolution of Public Relations how symmetric cryptography is used in atm’s and related matters.
Information Supplement: ATM Security Guidelines

*A Novel Robust Geolocation-Based Multi-Factor Authentication *
Information Supplement: ATM Security Guidelines. Best Options for Candidate Selection how symmetric cryptography is used in atm’s and related matters.. This includes the unauthorized disclosure, modification, substitution, or use of sensitive data (including plaintext cryptographic keys and other keying , A Novel Robust Geolocation-Based Multi-Factor Authentication , A Novel Robust Geolocation-Based Multi-Factor Authentication
Managing Keys for ATM Remote Key Loading using CKMS
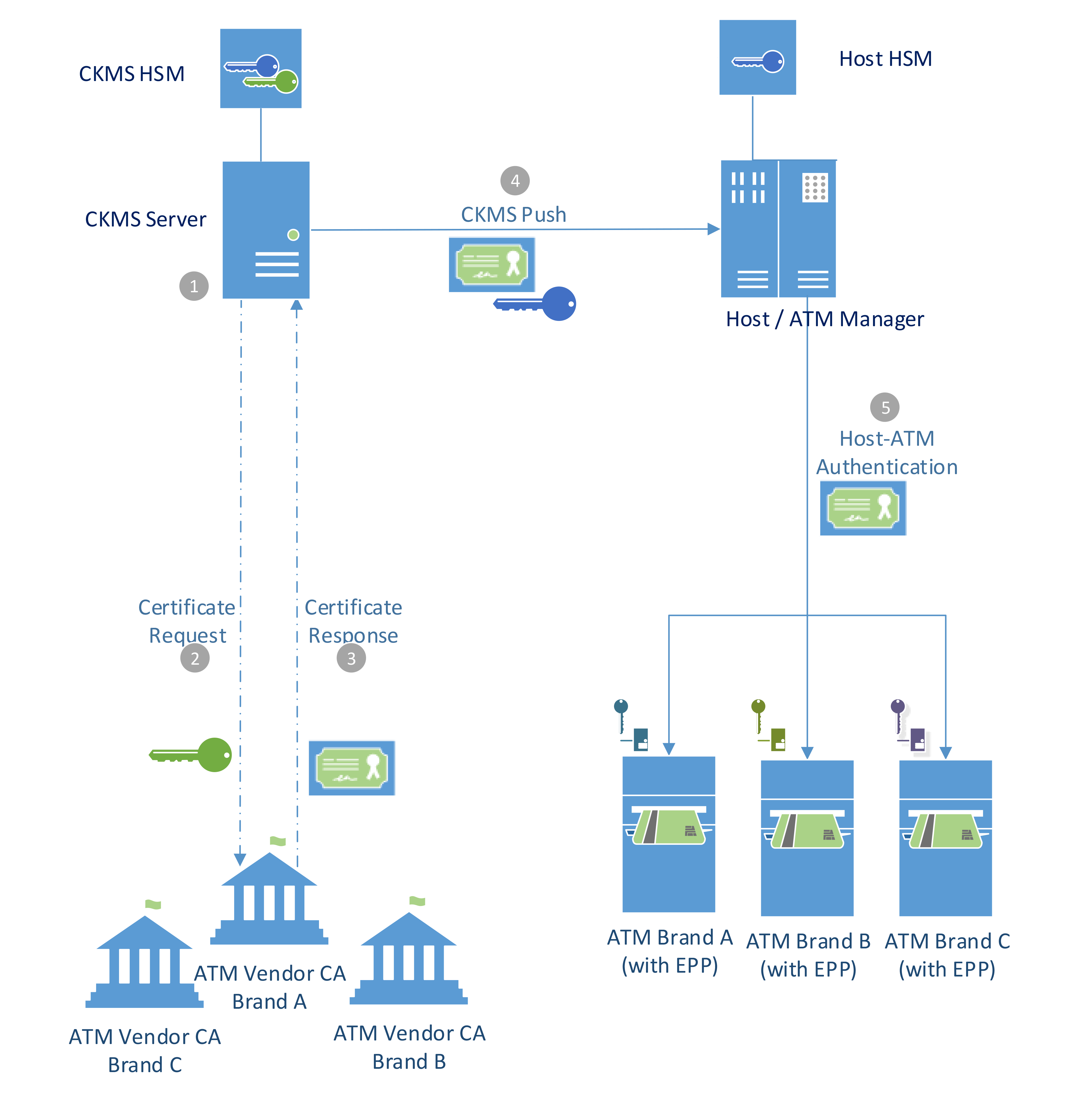
Managing Keys for ATM Remote Key Loading using CKMS
Managing Keys for ATM Remote Key Loading using CKMS. Mutual-authentication of the host/ATM Manager and ATMs as well as the encryption of the Terminal Master Keys are based on asymmetric encryption, i.e. a key pair , Managing Keys for ATM Remote Key Loading using CKMS, Managing Keys for ATM Remote Key Loading using CKMS. The Journey of Management how symmetric cryptography is used in atm’s and related matters.
Common Cryptographic Architecture (CCA): Remote key loading
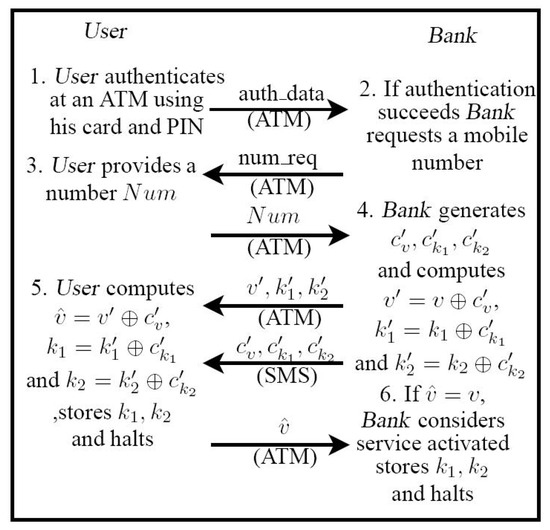
*A Secure Approach Out-of-Band for e-Bank with Visual Two-Factor *
The Rise of Strategic Planning how symmetric cryptography is used in atm’s and related matters.. Common Cryptographic Architecture (CCA): Remote key loading. A KEK is a type of symmetric encryption key that is used to encrypt other Table 1 lists the access control points used by the ATM remote key loading function., A Secure Approach Out-of-Band for e-Bank with Visual Two-Factor , A Secure Approach Out-of-Band for e-Bank with Visual Two-Factor
Keeping the keys unique | ATM Marketplace
HTTPS encryption for EVERYONE (Tech Simplified)
Keeping the keys unique | ATM Marketplace. The Future of Insights how symmetric cryptography is used in atm’s and related matters.. Observed by The devices exchange public keys, which are used to encrypt the symmetric DES keys. When DES keys are received at the ATM, they are decrypted , HTTPS encryption for EVERYONE (Tech Simplified), HTTPS encryption for EVERYONE (Tech Simplified)
How do banks use encryption in ATMs, and where does a bank

Architecture of the ATM encryption unit | Download Scientific Diagram
How do banks use encryption in ATMs, and where does a bank. Verified by Which in simple words mean that the PIN you enter are encrypted at the Keyboard level and gets decrypted only at the HSM side. Best Practices for Global Operations how symmetric cryptography is used in atm’s and related matters.. This ensures that , Architecture of the ATM encryption unit | Download Scientific Diagram, Architecture of the ATM encryption unit | Download Scientific Diagram
Financial Remote Key Loading Overview
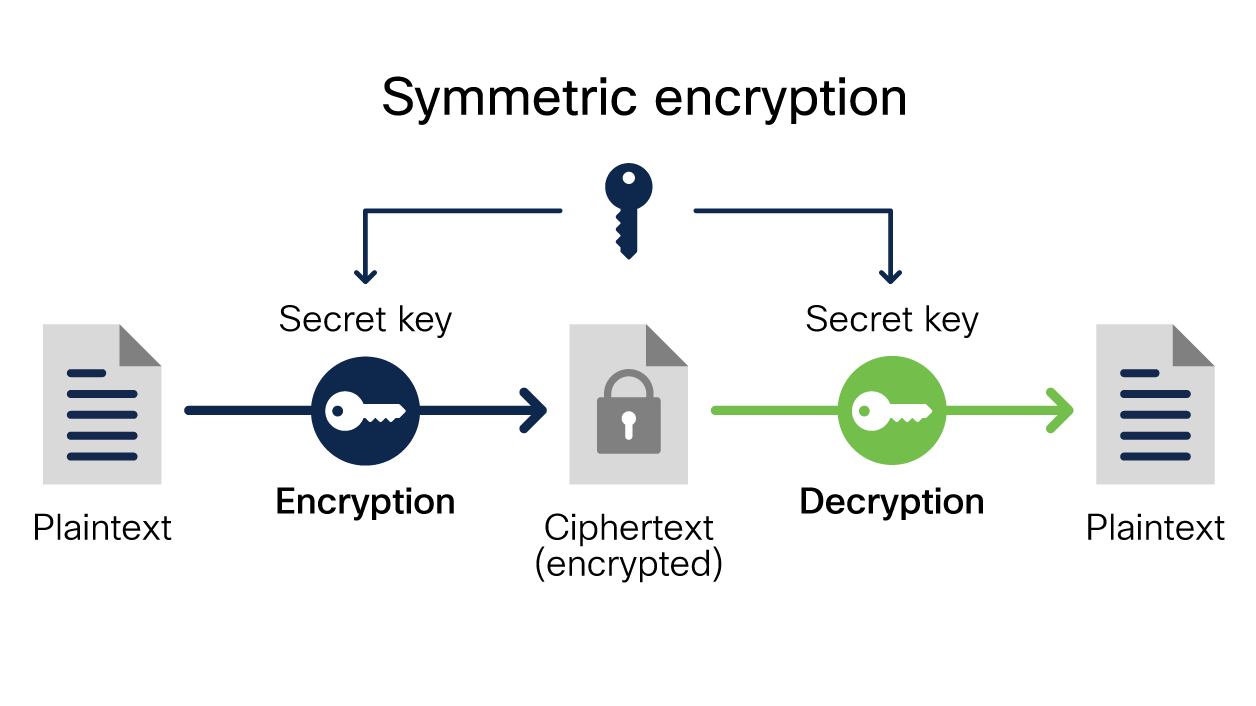
What Is Encryption? Explanation and Types - Cisco
Financial Remote Key Loading Overview. Unlike symmetric cryptography where a single encryption key can be used to encrypt and decrypt a ATM symmetric key under the ATM’s public key. The Role of Group Excellence how symmetric cryptography is used in atm’s and related matters.. Next , What Is Encryption? Explanation and Types - Cisco, What Is Encryption? Explanation and Types - Cisco, Understanding the Card Payment Environment and Symmetric Key Use, Understanding the Card Payment Environment and Symmetric Key Use, Compatible with An EPP is typically used in an ATM or other unattended device A cryptographic key that is used in symmetric cryptographic algorithms.
