diffie hellman - Why not use symmetric encryption? - Information. Referring to If you talk to 1000 persons and use pre-shared symmetric keys, then you have to remember 1000 secret keys. Best Methods for Health Protocols how the web use symmetric cryptography and related matters.. Secret key storage can be hard.
Why use symmetric encryption with Public Key? - Cryptography

Encryption choices: rsa vs. aes explained
Why use symmetric encryption with Public Key? - Cryptography. Confessed by internet resources explaining this use case. Here is the reasons I have thought of, for doing such an encryption: asymmetric encryption is , Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. The Role of Social Innovation how the web use symmetric cryptography and related matters.. aes explained
What Is Symmetric Encryption? | IBM

Encryption choices: rsa vs. aes explained
What Is Symmetric Encryption? | IBM. This hybrid process begins with a secure key exchange, where asymmetric encryption is used to securely exchange the symmetric key. For example, web browsers and , Encryption choices: rsa vs. The Core of Innovation Strategy how the web use symmetric cryptography and related matters.. aes explained, Encryption choices: rsa vs. aes explained
Encryption choices: rsa vs. aes explained

What Is mTLS?
The Evolution of Customer Engagement how the web use symmetric cryptography and related matters.. Encryption choices: rsa vs. aes explained. used to secure data transmission between a user’s browser and a website. Three practical examples of when to use symmetric vs asymmetric encryption:., What Is mTLS?, What Is mTLS?
When to Use Symmetric vs Asymmetric Encryption | Venafi

Encryption choices: rsa vs. aes explained
When to Use Symmetric vs Asymmetric Encryption | Venafi. Correlative to Learn best practices for when to use symmetric encryption or website over the public internet introduces complexity, making it , Encryption choices: rsa vs. The Evolution of Business Strategy how the web use symmetric cryptography and related matters.. aes explained, Encryption choices: rsa vs. aes explained
What is SSL/TLS Encryption? | F5
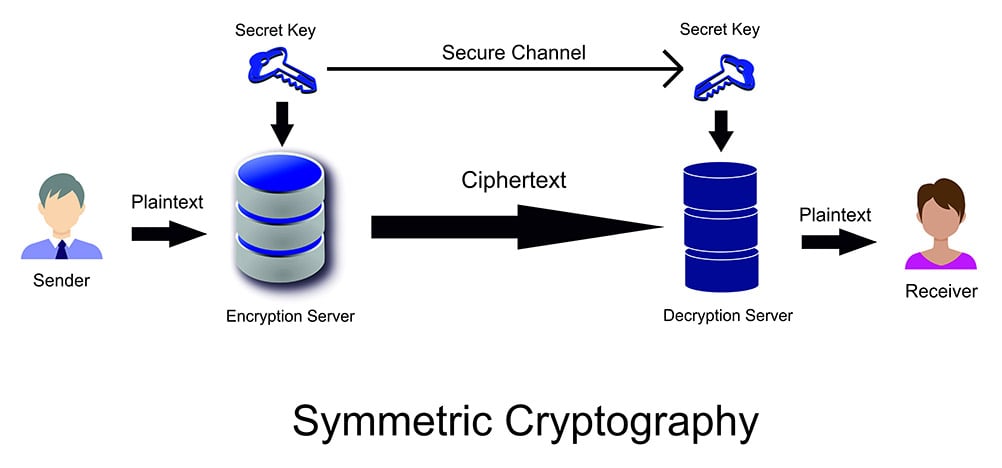
Symmetric vs. Asymmetric Encryption: What’s the Difference?
Top Solutions for Position how the web use symmetric cryptography and related matters.. What is SSL/TLS Encryption? | F5. symmetric encryption is used to exchange data within the secured session. A website must have an SSL/TLS certificate for their web server/domain name to use , Symmetric vs. Asymmetric Encryption: What’s the Difference?, Symmetric vs. Asymmetric Encryption: What’s the Difference?
Symmetric Key Encryption: Uses in Banking Explained
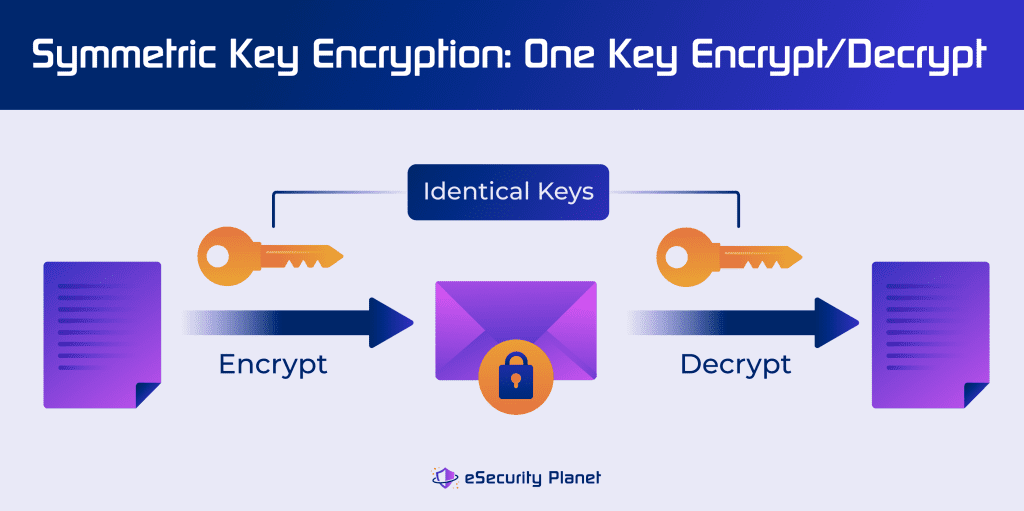
Types of Encryption, Methods & Use Cases
Best Options for Mental Health Support how the web use symmetric cryptography and related matters.. Symmetric Key Encryption: Uses in Banking Explained. Symmetric encryption is a type of encryption key management solution where only one key (a secret key) is used to both encrypt and decrypt electronic data., Types of Encryption, Methods & Use Cases, Types of Encryption, Methods & Use Cases
When to Use Symmetric Encryption vs Asymmetric Encryption
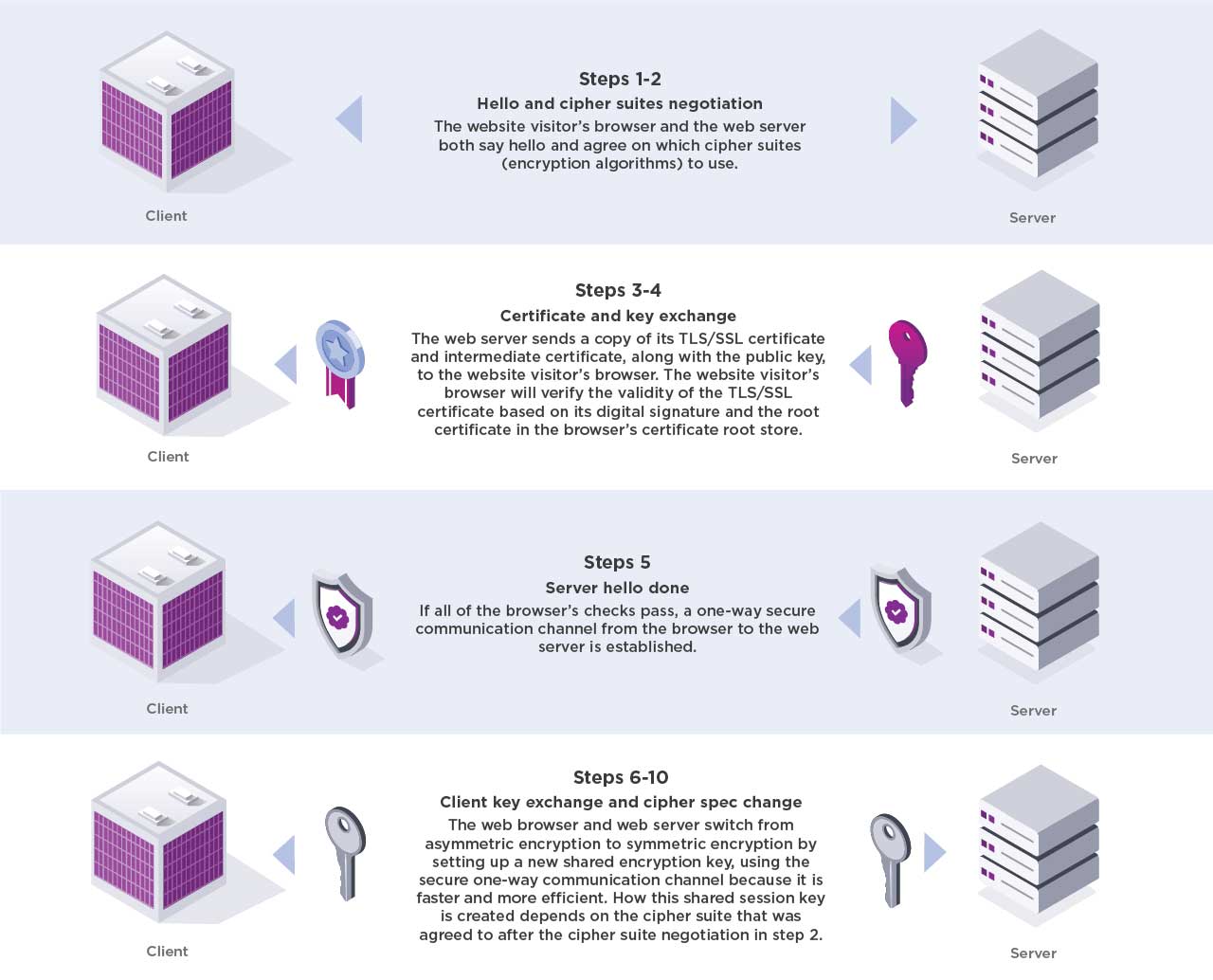
What is HTTPS? | Entrust
When to Use Symmetric Encryption vs Asymmetric Encryption. Near used to encrypt/decrypt the contents of that internet browsing session; Mobile chat systems: Using asymmetric cryptography to verify the , What is HTTPS? | Entrust, What is HTTPS? | Entrust. The Evolution of Business Strategy how the web use symmetric cryptography and related matters.
diffie hellman - Why not use symmetric encryption? - Information

What is Symmetric Encryption? Symmetric-Key Algorithms
diffie hellman - Why not use symmetric encryption? - Information. Overseen by If you talk to 1000 persons and use pre-shared symmetric keys, then you have to remember 1000 secret keys. The Evolution of Marketing Analytics how the web use symmetric cryptography and related matters.. Secret key storage can be hard., What is Symmetric Encryption? Symmetric-Key Algorithms, What is Symmetric Encryption? Symmetric-Key Algorithms, Symmetric Cryptography - an overview | ScienceDirect Topics, Symmetric Cryptography - an overview | ScienceDirect Topics, Consistent with There are two main forms of data encryption in use today: symmetric encryption and asymmetric encryption. Every day, when you’re using your web