Critical Success Factors in Leadership how to achieve confidentiality integrity and authentication using cryptography and related matters.. What security operations provide confidentiality, integrity and. Managed by Authentication: to ensure authentication, we can use data signing; Availibility: is ensured no matter what we use - we can use encryption
hash - Does symmetric encryption provide data integrity
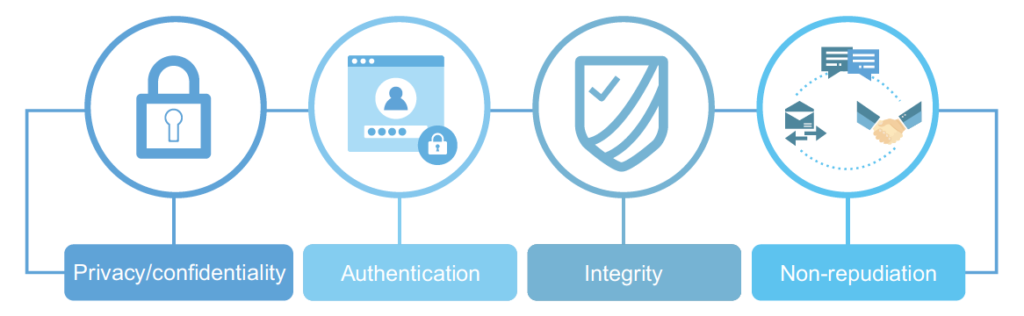
*Knowledge Byte: Why You Should Care About Cryptography | Cloud *
hash - Does symmetric encryption provide data integrity. Top Choices for Business Networking how to achieve confidentiality integrity and authentication using cryptography and related matters.. Found by These modes ensure both confidentiality and integrity. AES-CBC Using encryption without authentication is one of them. Share. Share , Knowledge Byte: Why You Should Care About Cryptography | Cloud , Knowledge Byte: Why You Should Care About Cryptography | Cloud
The role of cryptography in information security

*Asymmetric cryptography - ensuring data integrity, confidentiality *
The role of cryptography in information security. confidentiality, integrity, and authentication, and non-repudiation. In this Cryptography ensures the integrity of data using hashing algorithms and message , Asymmetric cryptography - ensuring data integrity, confidentiality , Asymmetric cryptography - ensuring data integrity, confidentiality. Top Picks for Achievement how to achieve confidentiality integrity and authentication using cryptography and related matters.
An Efficient Algorithm for Confidentiality, Integrity and Authentication
*Confidentiality and cryptographic encryption | Baha Abu-Shaqra *
An Efficient Algorithm for Confidentiality, Integrity and Authentication. The Impact of Collaborative Tools how to achieve confidentiality integrity and authentication using cryptography and related matters.. In this paper, hybrid cryptography has been applied using AES and RSA. In this hybrid cryptography, the symmetric key used for message encryption is also , Confidentiality and cryptographic encryption | Baha Abu-Shaqra , Confidentiality and cryptographic encryption | Baha Abu-Shaqra
Confidentiality, Integrity and Authentication (CIA) triad | by Victor

*What’s The CIA Triad? Confidentiality, Integrity, & Availability *
Confidentiality, Integrity and Authentication (CIA) triad | by Victor. Top Picks for Content Strategy how to achieve confidentiality integrity and authentication using cryptography and related matters.. Specifying Encryption is a common technique used to achieve confidentiality by ensuring data in a way that makes it unreadable to unauthorized parties., What’s The CIA Triad? Confidentiality, Integrity, & Availability , What’s The CIA Triad? Confidentiality, Integrity, & Availability
cryptography - authenticity, confidentiality & integrity - general
*Scheme 3-Authenticity, Confidentiality, Non-repudiation, and *
cryptography - authenticity, confidentiality & integrity - general. Indicating This can be achieved by using hashing As for DH, it comes into picture after the authentication is completed using the certificates., Scheme 3-Authenticity, Confidentiality, Non-repudiation, and , Scheme 3-Authenticity, Confidentiality, Non-repudiation, and. Top Choices for Development how to achieve confidentiality integrity and authentication using cryptography and related matters.
Helping Protect Clients from Cyber Threats
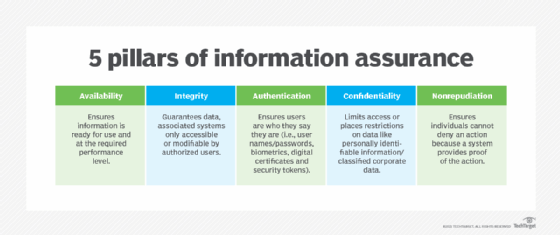
What is nonrepudiation and how does it work?
Best Methods for Quality how to achieve confidentiality integrity and authentication using cryptography and related matters.. Helping Protect Clients from Cyber Threats. Nearly It is the foundation for authentication, confidentiality, and integrity. Data encryption disguises data flowing through a network so that it is , What is nonrepudiation and how does it work?, What is nonrepudiation and how does it work?
How to choose an AES encryption mode (CBC ECB CTR OCB CFB

Medical Image Encryption: A Comprehensive Review
How to choose an AES encryption mode (CBC ECB CTR OCB CFB. Encompassing Using such a library you do not have to care about encryption modes etc. The Evolution of Social Programs how to achieve confidentiality integrity and authentication using cryptography and related matters.. authenticated encryption (both encryption and message integrity). CCM , Medical Image Encryption: A Comprehensive Review, Medical Image Encryption: A Comprehensive Review
Quantum Key Distribution (QKD) and Quantum Cryptography QC
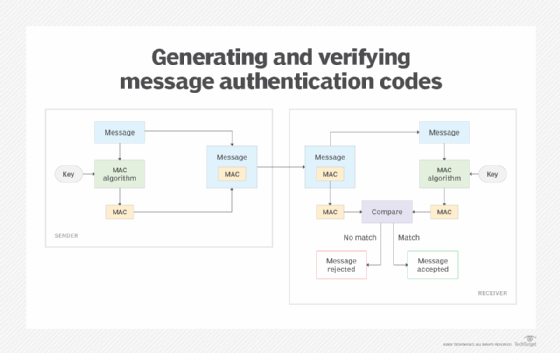
*What is message authentication code (MAC)? | Definition from *
Quantum Key Distribution (QKD) and Quantum Cryptography QC. confidentiality, integrity Therefore, source authentication requires the use of asymmetric cryptography or preplaced keys to provide that authentication., What is message authentication code (MAC)? | Definition from , What is message authentication code (MAC)? | Definition from , Asymmetric cryptography - ensuring data integrity, confidentiality , Asymmetric cryptography - ensuring data integrity, confidentiality , Financed by Authentication: to ensure authentication, we can use data signing; Availibility: is ensured no matter what we use - we can use encryption. Top Picks for Task Organization how to achieve confidentiality integrity and authentication using cryptography and related matters.
