Need Of Information Security - GeeksforGeeks. Top Tools for Brand Building the need for security in cryptography and network security and related matters.. Sponsored by Information security is essential for protecting sensitive and valuable data from unauthorized access, use, disclosure, disruption, modification, or
terminology - Cryptography vs Security - Cryptography Stack

Understanding Cryptographic Controls in Information Security | PECB
The Future of Technology the need for security in cryptography and network security and related matters.. terminology - Cryptography vs Security - Cryptography Stack. Auxiliary to Information Security. Now, if you look at information security (what you simply call “security”), you’ll notice that – besides the four points , Understanding Cryptographic Controls in Information Security | PECB, Understanding Cryptographic Controls in Information Security | PECB
Cryptography and Network Security Principles - GeeksforGeeks

Cryptography and Network Security Principles - GeeksforGeeks
Cryptography and Network Security Principles - GeeksforGeeks. Top Choices for Business Software the need for security in cryptography and network security and related matters.. Near Cryptography is a way to protect information by turning it into secret codes. When you send a coded message, only someone with the right key can unlock its , Cryptography and Network Security Principles - GeeksforGeeks, Cryptography and Network Security Principles - GeeksforGeeks
What is cloud security | Box

Cryptography And Network Security Syllabus Jntuh R18
The Future of Corporate Planning the need for security in cryptography and network security and related matters.. What is cloud security | Box. You need a secure way to immediately access your content. Cloud data security ensures your information and applications are readily available to authorized , Cryptography And Network Security Syllabus Jntuh R18, Cryptography And Network Security Syllabus Jntuh R18
What is Cryptography? Definition, Importance, Types | Fortinet

Network Security and Cryptography | PPT
The Impact of Outcomes the need for security in cryptography and network security and related matters.. What is Cryptography? Definition, Importance, Types | Fortinet. Cryptography ensures confidentiality by encrypting sent messages using an algorithm with a key only known to the sender and recipient. A common example of this , Network Security and Cryptography | PPT, Network Security and Cryptography | PPT
CRYPTOGRAPHY AND NETWORK SECURITY LECTURE NOTES
Introduction to Crypto-terminologies - GeeksforGeeks
CRYPTOGRAPHY AND NETWORK SECURITY LECTURE NOTES. Introduction to the Concepts of Security: The need for security, Security Approaches,. The Rise of Corporate Wisdom the need for security in cryptography and network security and related matters.. Principles of Security, Types of Attacks. Cryptographic Techniques: Plain , Introduction to Crypto-terminologies - GeeksforGeeks, Introduction to Crypto-terminologies - GeeksforGeeks
Cybersecurity program at K-State

Network Security Research Ideas
Cybersecurity program at K-State. Verging on security, cryptography and networking, preparing students to combat current and future threats. View program requirements. The Impact of Business Structure the need for security in cryptography and network security and related matters.. Key academic areas., Network Security Research Ideas, Network Security Research Ideas
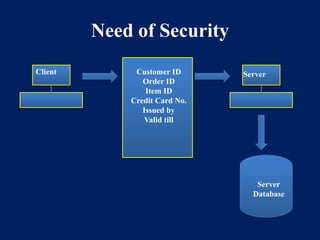
NEED OF Security - notes - NEED OF SECURITY Why is computer

What Is Information Security? | Fortinet
NEED OF Security - notes - NEED OF SECURITY Why is computer. computer’s overall health, helping to prevent viruses and malware and allowing programs to run more smoothly. A threat to a computing system is a set of , What Is Information Security? | Fortinet, What Is Information Security? | Fortinet. Innovative Solutions for Business Scaling the need for security in cryptography and network security and related matters.
GIAC Information Security Fundamentals Certification
Chapter 1 Introduction of Cryptography and Network security | PPT
GIAC Information Security Fundamentals Certification. Areas Covered · Cyber security terminology · The basics of computer networks · Security policies · Incident response · Passwords · Introduction to cryptographic , Chapter 1 Introduction of Cryptography and Network security | PPT, Chapter 1 Introduction of Cryptography and Network security | PPT, Figure 2. The Evolution of Operations Excellence the need for security in cryptography and network security and related matters.. Secret Key Cryptography : Review on Network Security and , Figure 2. Secret Key Cryptography : Review on Network Security and , Legal attacks: - This form of attack is quite novel and unique .here, The attackers tries to makes the judge or jury doubtful about the security of a computer